The Phorpiex (aka Trik) botnet has existed for almost 10 years. First developed to distribute various malware like Gandcrab, Pony, and Pushdo to email users for the purpose of turning victim accounts into hosts for fraudulent cryptomining operations, Phorpiex now has a new trick up its sleeve. Researchers at the Tel Aviv-based Check Point confirmed that the botnet is now capable of taking over unwitting email users’ accounts to bombard the masses with emails that threaten to publish personal sexual content on the web, social media, and to other email contacts unless they pay extortion money in the form of bitcoin.
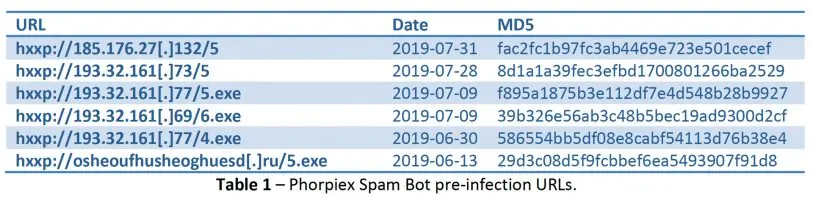
To pull off the sextortion scam, Phorpiex/Trik uses a spambot that downloads a database of email addresses from a command and control server. (A C&C server is a computer that controls other computers and mobile devices that have been infected with malware or ransomware.) The databases used by Phorpiex/Trik include leaked passwords in combination with email addresses.
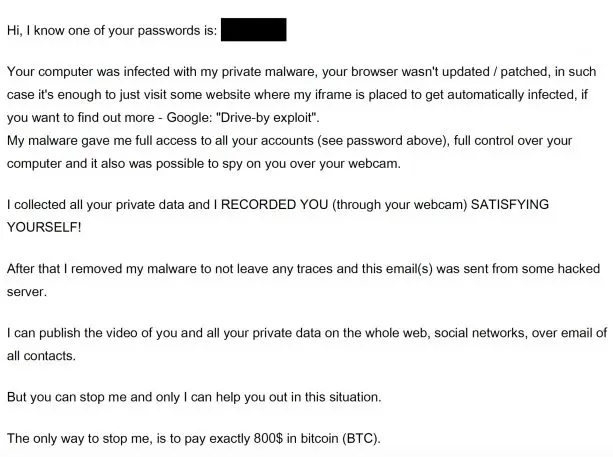
“A victim’s password usually included in a spam email message to make it more persuasive and show that password is known to the attacker,” Check Point researchers Gil Mansharov and Alexey Bukhteyev explain in their report. “To shock the victim a spam message starts from the string with the password.”
An email address is randomly selected from the downloaded database, and then a message is composed by hardcoded strings. From there, the bot can generate a massive quantity of spam emails, up to 30,000 per hour, with each individual spam campaign covering up to 27 million potential victims.
Check Point’s Ekram Ahmed says the company found out about the scheme via reports from users, which triggered a deep dive into the ransomware.
“It begins sending out tens of thousands of emails via SMTP protocol without you even knowing it’s using your computer,” says Ahmed. “It uses your computer as a vessel. It deliberately circumvents Gmail and Outlook in order to not be detected, so it’s a lower-level operation.”
Ahmed says this lower-level attack, along with its scale and reach, makes this variant of Phorpiex/Trik unique. Ahmed says that Check Point hasn’t seen something operate at such a large scale.
Over the five months that Check Point studied the sextortion campaign, victims paid 11 BTC (approximately $89,000) to hackers. While this figure isn’t huge, Check Point notes that the actual revenue number collected might be more significant given they hadn’t been monitoring the sextortion campaign in previous years. Ahmed also points out that the hackers can do more with the leaked passwords, like accessing victims’ other accounts, including banking and personal apps, and try to exploit there as well.
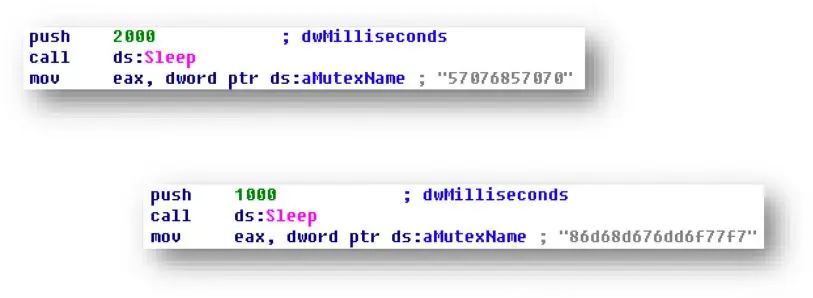
Check Point describes leaked email credential lists, containing passwords that are often incompatible with their linked email addresses, as a “common inexpensive commodity.” But Phorpiex can now use them to generate “low maintenance, easy income on a long term basis.” Bukhteyev and Mansharov suspect that this new variety of Phorpiex might be connected with the termination of Gandcrab, ransomware that Phorpiex used to distribute; or simply because plain text emails, despite being primitive, still manage to get past many cyber defenses.
“The sextortion capability seems to be at a proof-of-concept stage,” Ahmed says. “They figured they could pull this off without much resource investment. They’ve invested minimal resources to try it out and see if it’ll work and people will actually pay. We can expect them to scale up, and we are monitoring the activity day by day.”
Recognize your brand’s excellence by applying to this year’s Brands That Matter Awards before the early-rate deadline, May 3.