Increasingly Internet-connected office heating and lighting systems could be a target for hackers seeking a backdoor into corporate networks, warns IBM’s X-Force security research group.
A recent survey of building automation system managers found that 84% of managers run at least one system connected to the Internet, and nearly half had systems connected to a traditional corporate IT network, says Chris Poulin, a research strategist with IBM X-Force. And with some automation vendors still figuring out how best to secure their systems, these systems can provide an entry path for hackers looking to steal data from company networks—or even an avenue to cause physical damage by tampering with climate control systems themselves.
“For example, you could affect the temperature of a data center, and cause not just a standard denial of service attack,” says Poulin. “You could actually melt down the systems by heating up the computer room.”
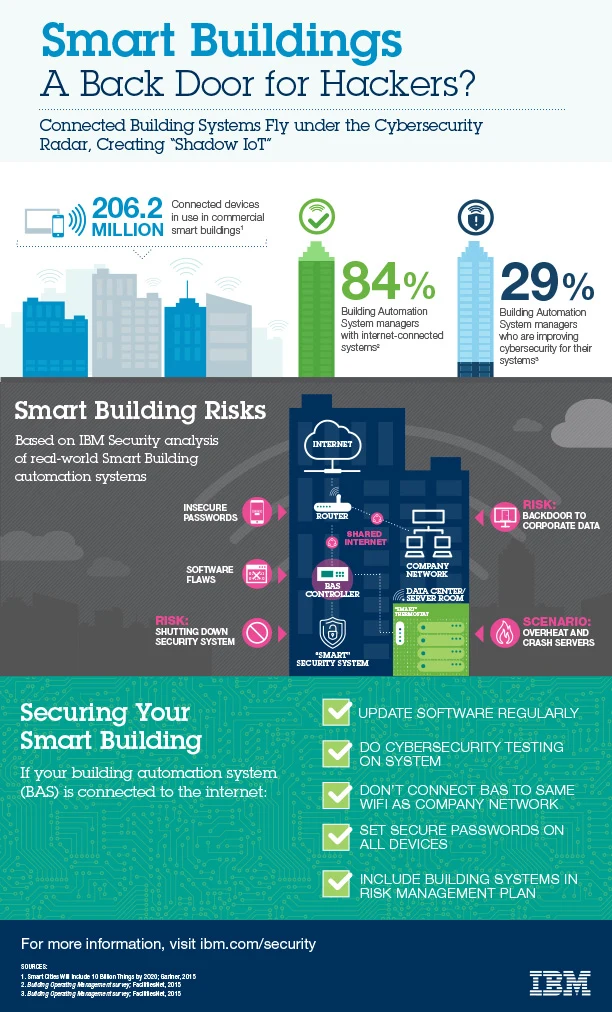
In a recent test, IBM researchers were able to exploit a series of security holes, from software bugs to passwords stored unencrypted and used across multiple systems, to gain access to an office building’s automation system that managed thermostats and other sensors, the company said in a white paper released this week. The researchers were even able to obtain passwords giving them access to a server managing several buildings under the same management, the company says.
IBM worked with building management and the affected vendors to fix the security holes, Poulin says.
“We always consider that a success when we can find something before anyone else and help the vendor to patch it up,” he says.
The company advises building automated system managers to take basic precautions such as keeping up to date with software patches and avoiding password reuse and configuring firewalls to limit remote access to automation systems as much as business requirements allow.
Companies can also use techniques like two-factor authentication to make it harder for attackers to gain access to automation systems and monitor network traffic and login attempts to catch suspicious activity quickly, according to the white paper.
Recognize your brand’s excellence by applying to this year’s Brands That Matter Awards before the early-rate deadline, May 3.
