This year tech giants, governments, and even the humble sandwich chain have proved that we can trust no one with our personal data. At best, these companies were woefully underprepared to keep our data safe. At worst, they allowed the data we gave them to help others influence our fragile democracy.
When it came to data scandals and breaches in 2018, the only good news was in the form of the European Union’s progressive General Data Protection Regulation (GDPR) legislation and the protections it provides for consumers affected by data breaches. Thanks to GDPR, companies must now disclose data breaches promptly or face massive fines. The downside: Americans don’t have any such protections—even as cyberattacks intensify.
What’s even more depressing is the data scandals and breaches we’re highlighting here are just the tip of the iceberg of all the misuse that our data endured during the year. According to DarkReading, there were an estimated 3,676 data breaches in the first nine months of 2018 alone, putting it on track to have the second-most number of reported breaches in a single year. So be warned: while most end-of-year roundups are positive or even downright poignant, this one’s going to be a big bummer.
Facebook’s problems
Without a doubt, this was the biggest data scandal of 2018, though technically it began years earlier. On March 17, 2018, the Guardian and the New York Times broke the story of how British political consulting firm Cambridge Analytica harvested the data of at least 87 million Facebook users without their knowledge after obtaining it from people who partook in a quiz app. Cambridge Analytica then sold this data to the Donald Trump campaign, which used it to target election messages at Facebook users in the 2016 presidential election campaign.
The biggest problem with the quiz app was that 87 million people didn’t take it–at most, several hundred thousand did. The quiz app exposed a loophole in the Facebook API that allowed it not to just take the data of the quiz users themselves, but of all their friends as well–people who never even took the quiz or had ever interacted with the app in any way. (Incidentally, one of the academic researchers who helped build the app was hired by Facebook in 2015, but the company hasn’t answered questions about what it knew about his role before it dismissed him in September.)
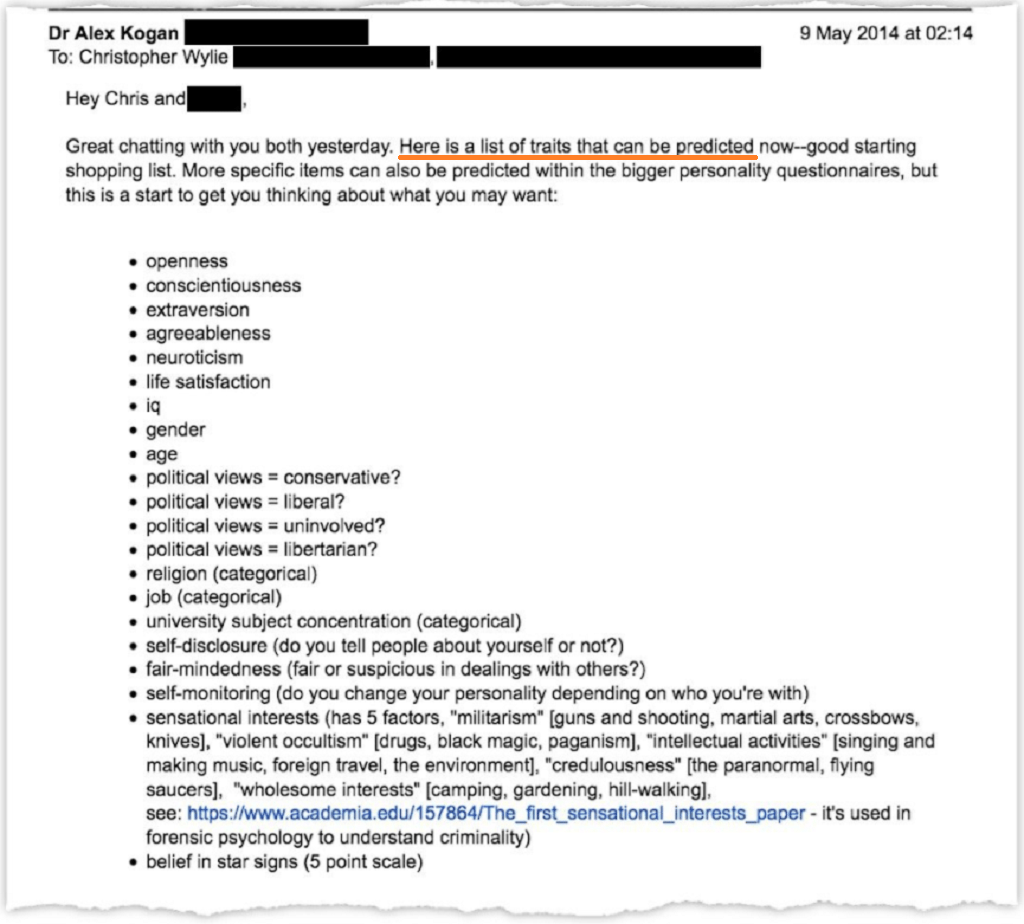
Oh, and Facebook also had a major data breach this year as well. Disclosed in September, the breach impacted at least 30 million Facebook users and saw cyber thieves make off with data on where they live, when they were born, what their relationship status is, and in some cases, their recent searches.
Fitness app Polar exposes the personal information of U.S. military and security personnel
Speaking of apps, it wasn’t a great year for Polar, a popular fitness app used by many in the military, and, apparently, the NSA and Secret Service. We know this because Polar had such lax data security that researchers were easily able to track the app’s military and security services users as they exercised around their bases. Not only that, but the next-to-nonexistent data protection features in the app also allowed virtually anyone to see the military and security officials’ names, heart rates, and even where they lived.
By the time the researchers went public with their findings, they were able to procure the personal information of more than 6,460 U.S. military and security personnel, the Washington Post reported. That included personnel stationed at military bases overseas, such as Guantanamo Bay Naval Base and Camp Lemonnier in Djibouti, the main base of operations for U.S. Africa Command in the Horn of Africa.
Exactis exposes nearly everything about 230 million Americans
Data breaches that screw a small portion of our military personnel are bad enough. But how about such weak-ass data security that leaves 230 million American citizens and another 110 million U.S. businesses exposed? Because that’s exactly what happened when it was discovered in June that a Florida marketing firm called Exactis left the records of 340 million people and businesses on a publicly accessible server that anyone could access.
Exactis left exposed a staggering two terabytes of information on people and businesses. And we’re not just talking about names and emails (though those were included as well). We’re also talking over 400 other personal characteristics, such as if someone is a smoker or owns pets, their religion, whether they have children, and their interests. It’s as if Christmas came early for identity thieves this year.
Aadhaar login breach reveals data about everyone in India
But let’s cut Exactis some slack, shall we? I mean, what are the records of 230 million Americans being left vulnerable compared to all 1.1 billion people in India? Because that’s what happened with India’s growing Aadhaar biometric system. Aadhaar, run by the Indian government, is the largest biometric ID system in the world, which includes photographs, fingerprints, home addresses, and other personal information of virtually every citizen in the country.
So you think the Indian government would be alarmed when an investigative journalist discovered that people on WhatsApp were selling the login credentials to the Aadhaar system, which allowed the user to enter anyone’s Aadhaar number to access all the data stored on them. And the sellers were selling the login credentials for the equivalent of roughly $7 USD.
But nope. Indian officials seemed angrier that the scheme had been discovered by the investigative journalist, and filed a criminal complaint against her for “misreporting.” In March, a security researcher showed ZDNet that the system was vulnerable; the government again issued a denial.
Marriott hack affects half a billion people who stayed at its hotels
Yeah, that’s half a billion, with a B. This hack was revealed by Marriott on November 30, 2018–but it had been going on continuously since 2014, affecting guests who stayed at Marriot’s Starwood properties including W Hotels, St. Regis, Sheraton, Westin, and more.
The hackers—suspected to be connected to Beijing—basically got away with virtually every data point of 327 million of the half billion guests affected, including name, mailing address, phone number, email address, passport number, Starwood Preferred Guest (“SPG”) account information, date of birth, gender, arrival and departure information, reservation date, communication preferences, payment card numbers, and payment card expiration dates. The “lucky” other 173 million guests only had their names and sometimes other data including mailing address, email address, or “other information” stolen.
Panera Bread–would you like a side of identity theft with your Sierra Turkey?
And by god, people weren’t even safe from sandwich shops leaking their data. In April, it was disclosed that a security researcher had discovered that popular sandwich chain Panera Bread’s website was leaking customers’ records in plain text and included names, emails, physical addresses, birthdays, and the last four digits of the customer’s credit card number.
The most infuriating thing about this was that the security researcher had been contacting Panera Bread for eight months to fix the flaw. A week after the researcher originally contacted Panera, the company said the leak had been fixed, but the researcher could continue to access data via the leak for another eight months, which is when he went public. It was only then that Panera took its website offline to fix the leak. Though total numbers of people affected are unknown, security researchers say it could be as high as 37 million people.
Related: When passwords get stolen, this Australian guy alerts the world
Google Plus exposed the data of 500,000 people, then 52.5 million
Last on this list, but not least, is Google. The company fessed up to a potential data breach of its virtually unused Google+ social network in October after the Wall Street Journal broke the story that Google had earlier in the year discovered a bug that could have exposed private data for up to 500,000 users since 2015. The data includes the names, emails, ages, genders, and occupations of Google+ users.
But again, just as Panera did, Google didn’t disclose this potential data breach for almost seven months after they discovered it, fearing doing so would hurt public perception of the company and increase regulatory scrutiny. Oh, and in December the company found another data breach in a Google+ API that left the name, email address, occupation, and age of 52.5 million Google+ users exposed for six days. This time Google waited almost a month before alerting users.
See a trend here? The way Google and Panera responded to their data leaks–by keeping them private from the public until getting caught–demonstrates that the U.S. needs a robust set of privacy protections that mimic the European Union’s GDPR.
Despite all the things we lost in 2018, at least the year gave us something to take with us: a reminder that we can trust no one with our data.
Recognize your brand’s excellence by applying to this year’s Brands That Matter Awards before the early-rate deadline, May 3.