Users of password manager LastPass should beware of phishing attempts that impersonate the program’s browser extension pop-ups to steal their passwords, warns security expert Sean Cassidy.
Cassidy presented a proof-of-concept demonstration this week at the ShmooCon security convention, showing how malicious websites can generate in-browser pop-ups that mimic—in some cases, down to the individual pixels—LastPass’s login prompts.
“I was using LastPass, and I was on some random website, and it popped up a notification that I had been logged out, and I went to go click the notification, because it was just displayed at the top of the web page,” says Cassidy, who is the CTO of security firm Praesidio. “I clicked it, and then I verified that it was actually LastPass, and then I thought, ‘You know what? I can do this same thing.’”
LastPass stores login credentials for multiple websites locked behind a single master password, so users don’t have to memorize or write down individual usernames and passwords. When visiting a site with credentials stored in LastPass and not logged in to the program, LastPass will generate an in-browser pop-up prompting the user to enter the LastPass password.
And since the pop-up is generated with the same kind of code used to build websites, there’s nothing to prevent hackers from generating an identical-looking prompt and stealing users’ LastPass passwords—potentially giving them access to each of the user’s other passwords, Cassidy says.
“The problem with most defenses for phishes is you train your users to say, this is what a phishing email looks like, don’t click it,” he says. “But in this case, the phish is exactly the same HTML and CSS, so there’s no way to tell which is real and which is fake.”
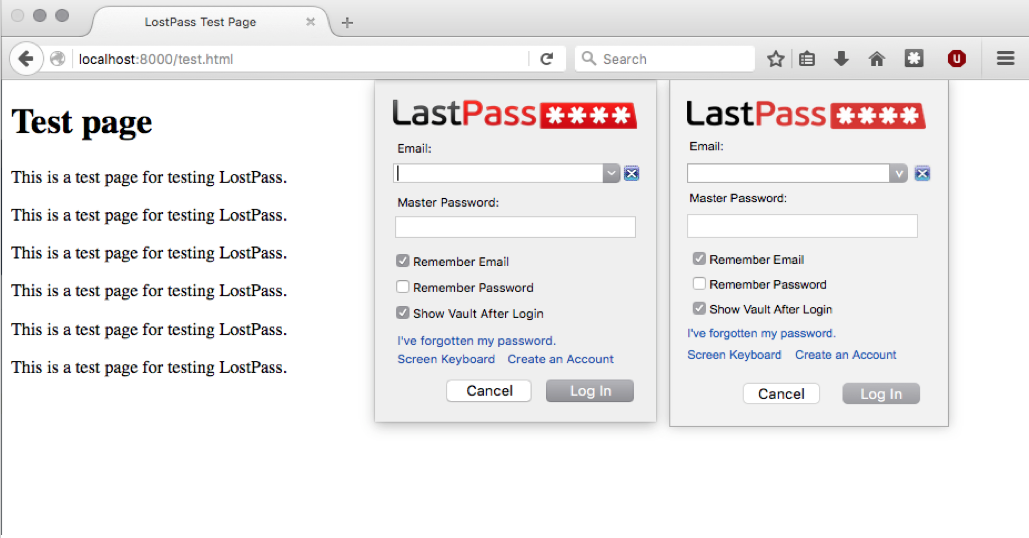
Cassidy says LastPass has told him they’re taking steps to make such phishing attacks harder, which the company confirmed in an email to Fast Company on Thursday.
“We did work directly with Sean Cassidy, and can confirm this is a phishing attack, not a vulnerability in LastPass,” a company spokeswoman wrote. “However, we’ve released an update that will prevent a user from being logged out by the phishing tool, thereby mitigating the risk of the phishing attack. In addition, LastPass has a built-in security alert to let you know when you’ve entered your master password into a non-LastPass web form.”
Cassidy says he felt an obligation to make the vulnerability known, particularly since it’s relatively easy to construct a phishing attack based on the issue, though he’s not aware of any such attacks yet.
“Unlike a very advanced buffer overflow, or something that only a few people would know how to exploit, instead, anyone who knows HTML and CSS could exploit this, and very little coding is involved,” he says.
He recommends that IT departments make sure their users are aware of the issue and urge users to always interact with LastPass by clicking on the program’s icon, rather than responding to its pop-ups—just as users concerned about phishing might navigate directly to a bank’s site or app rather than clicking on emailed links.
Recognize your brand’s excellence by applying to this year’s Brands That Matter Awards before the early-rate deadline, May 3.
